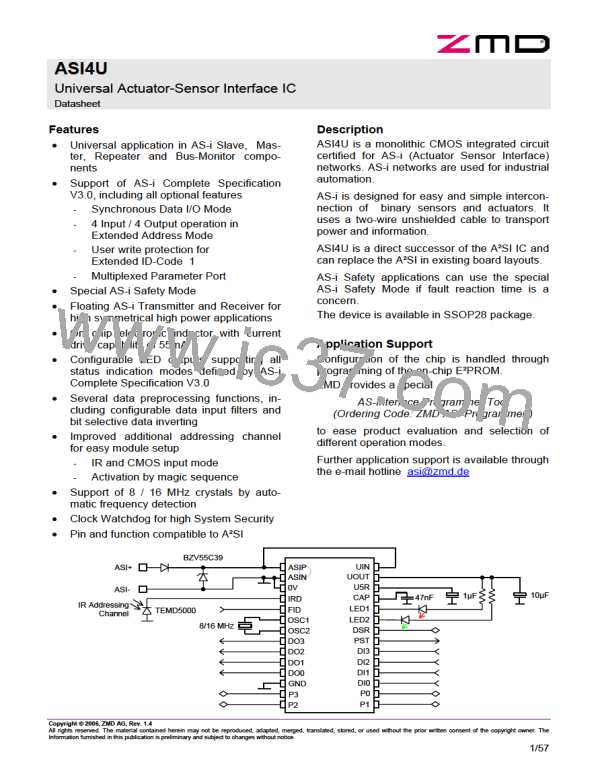
ZENTRUM MIKROELEKTRONIK DRESDEN AG
“ASI for you” IC
Datasheet
2.5 E²PROM
The ASI4U provides an on-chip E²PROM with typical write times of 12.5 ms and read times of 110ns. For secu-
rity reasons the memory area is structured in two independent data blocks and a single bit Security flag.
The data blocks are named User Area and Firmware Area. The Firmware Area contains all manufacturing re-
lated configuration data (i.e. selection of operational modes, ID codes, …). It can be protected against undesired
data modification by setting the Program_Mode_Disable flag to ‘1’.
The User Area contains only such data that is relevant for changes at the final application (i.e. field installation
of slave module). The environment, where modifications of the user data may become necessary, can some-
times be rough and unpredictable. In order to ensure a write access cannot result in an undetected corruption of
E²PROM data, additional security is provided when programming the User Area.
Any write access to the User Area (by calls Address_Assignment or Write_ID_Code1) is accompanied by two
write steps to the Security flag, one before and one after the actual modification of user data.
The following procedure is executed when writing to the User Area of the E²PROM:
1. The Security flag is programmed to ‘1’.
2. The content of the Security flag is read back, verifying it was programmed to ‘1’.
3. The user data is modified.
4. A read back of the written data is performed.
5. If the read back has proven successful programming of the user data, the Security flag
is programmed back to ‘0’.
6. The content of the Security flag is read back, verifying it was programmed to ‘0’.
In addition to a read out of the data areas, the Security flag of the E²PROM is also read and evaluated during IC
initialization. In case the value of the Security flag equals ‘1’ (i.e. due to an undesired interruption of a User Area
write access), the entire User Area data is treated as corrupted and the Slave Address is set to 0x0 in the corre-
sponding volatile shadow registers during initialization. Thus the programming of the User Area data can be
repeated.
Table 7: E²PROM Content
ASI4U internal
Bit
Position
EEPROM Cell Content
EEPROM Register Content
E²PROM Address [hex]
0
1
2
2
0 … 3
A0 … A3
Slave address low nibble
Slave address high nibble
ID_Code_Extension_1
0
A4
0 … 2
3
ID1_Bit0 … ID1_Bit2
ID1_Bit3
ID_Code_Extension_1, A/B slave selection
in extended address mode
3 … 7
Not implemented
8
9
A
B
0 … 3
0 … 3
0 … 3
0
ID_Bit0 … ID_Bit3
ID2_Bit0 … ID2_Bit3
IO_Bit0 … IO_Bit3
Multiplex_Data
ID_Code
ID_Code_Extension_2
IO_Code
Multiplexed bi-directional Data Port mode
1
Multiplex_Paramter
Multiplexed bi-directional Parameter Port
mode
2
3
P0_Watchdog_Activation
Watchdog_Active
Watchdog can be activated/deactivated by
the logic value at parameter pin P0.
Watchdog_Active must not be set.
Communication watchdog is continuously
activated.
Copyright © 2006, ZMD AG, Rev.1.4
All rights reserved. The material contained herein may not be reproduced, adapted, merged, translated, stored, or used without the prior written consent of the copyright owner. The
Information furnished in this publication is preliminary and subject to changes without notice.
18/57
 ZMD [ Zentrum Mikroelektronik Dresden AG ]
ZMD [ Zentrum Mikroelektronik Dresden AG ]